Most service disruptions are not random events. They are the result of changes made without a full understanding of the systems involved. When your IT environment is a black box, every update is a gamble and every incident response starts from zero. Effective ITIL configuration management replaces that uncertainty with a clear, reliable map of your entire infrastructure.
This guide walks you through the fundamentals of building a strong configuration management practice, from defining configuration items to establishing a reliable CMDB. You will explore the core principles, benefits, and best practices that transform this discipline from a complex chore into a strategic advantage.
With the right approach and an intuitive platform, you can gain the visibility needed to manage change, resolve incidents faster, and optimize operations.
Key takeaways
- Complete IT map: configuration management gives you a complete map of your IT environment, helping you make smarter decisions and solve problems faster when things go wrong.
- Single source of truth (CMDB): a well-maintained CMDB acts as your single source of truth, showing not just what you have but how everything connects together across your entire infrastructure.
- Platform transformation: platforms like monday service transform configuration management with AI-powered discovery and visual dependency mapping, making complex relationships easy to understand without technical expertise.
- Data accuracy: automated discovery and real-time monitoring are essential for keeping your configuration data accurate as your IT environment constantly changes and evolves.
- Actionable insights: integration with other ITIL practices like change and incident management multiplies your investment, turning configuration data into actionable insights for faster resolutions.
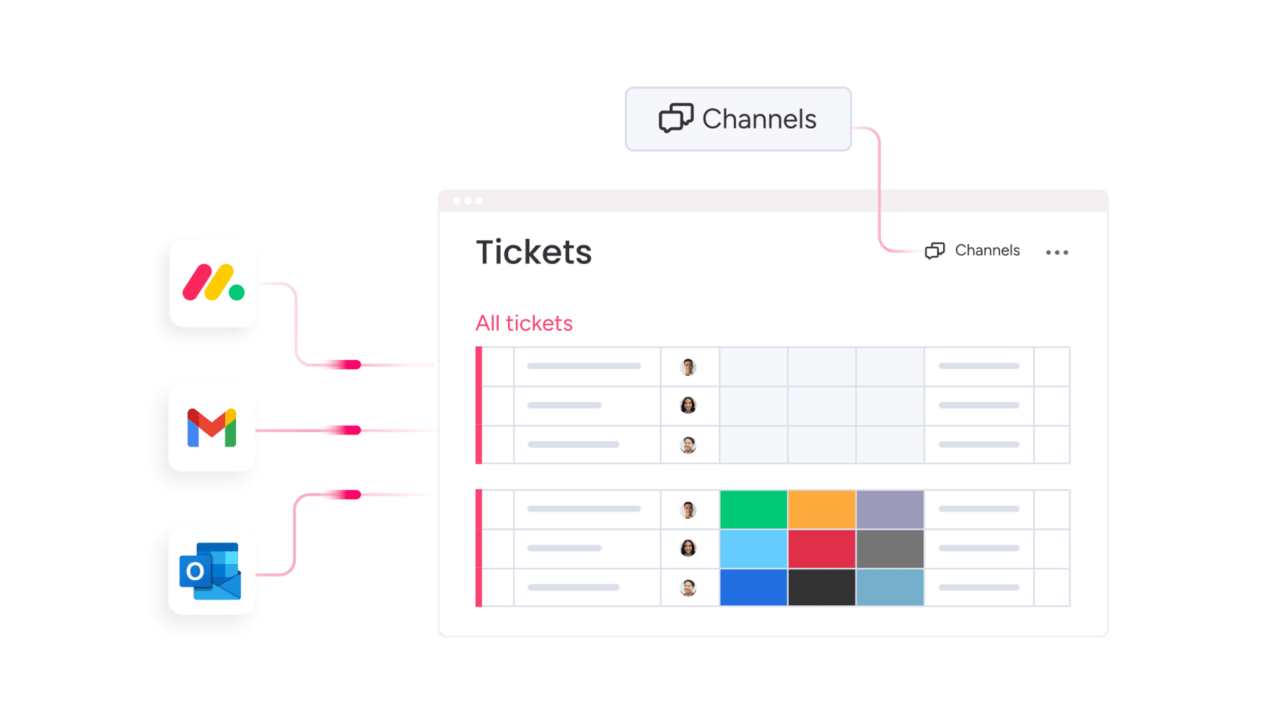
What is configuration management in ITIL?
In ITIL, configuration management provides a verified, up-to-date view of every component that supports your IT services and operations. It shows what exists in your environment, where it lives, who owns it, and how each part relates to the others.
This reliable data becomes the backbone of decision-making. Whether you’re planning a change or diagnosing an incident, you can act with confidence instead of relying on guesswork. The practice covers all configuration items — hardware, software, documentation, and key personnel — and tracks each one throughout its lifecycle so teams can maintain stability and manage change more effectively.
Definition and purpose
According to the ITIL framework, configuration management ensures accurate information about your services and their components is available when and where you need it. In practice, this means you always know what you have, where it is, and how it connects to everything else.
The main purpose? To give you a single source of truth for all IT decisions. When you’re planning a change or responding to an incident, you need reliable data about your environment — configuration management provides exactly that.
Configuration items explained
Configuration items (CIs) are any components you need to manage to deliver IT services. These aren’t just servers and laptops; they include anything that could impact service delivery.
Typical configuration items include::
- Hardware: servers, workstations, network devices, storage systems.
- Software: operating systems, applications, databases, middleware.
- Documentation: process guides, network diagrams, service manuals.
- People: key personnel with critical knowledge or access.
Each CI gets tracked throughout its entire lifecycle, from purchase to retirement.
Role in service management
Configuration management acts as the foundation for other ITIL practices, including service request management. Change teams use it to understand what might break when they update systems, a critical function of IT change management. Incident teams rely on it to quickly identify affected services during outages.
With configuration management, you gain the complete operational awareness needed to navigate your IT environment confidently. Modern solutions like monday service connect configuration data directly to your service workflows, so teams always have the context they need to make informed decisions.
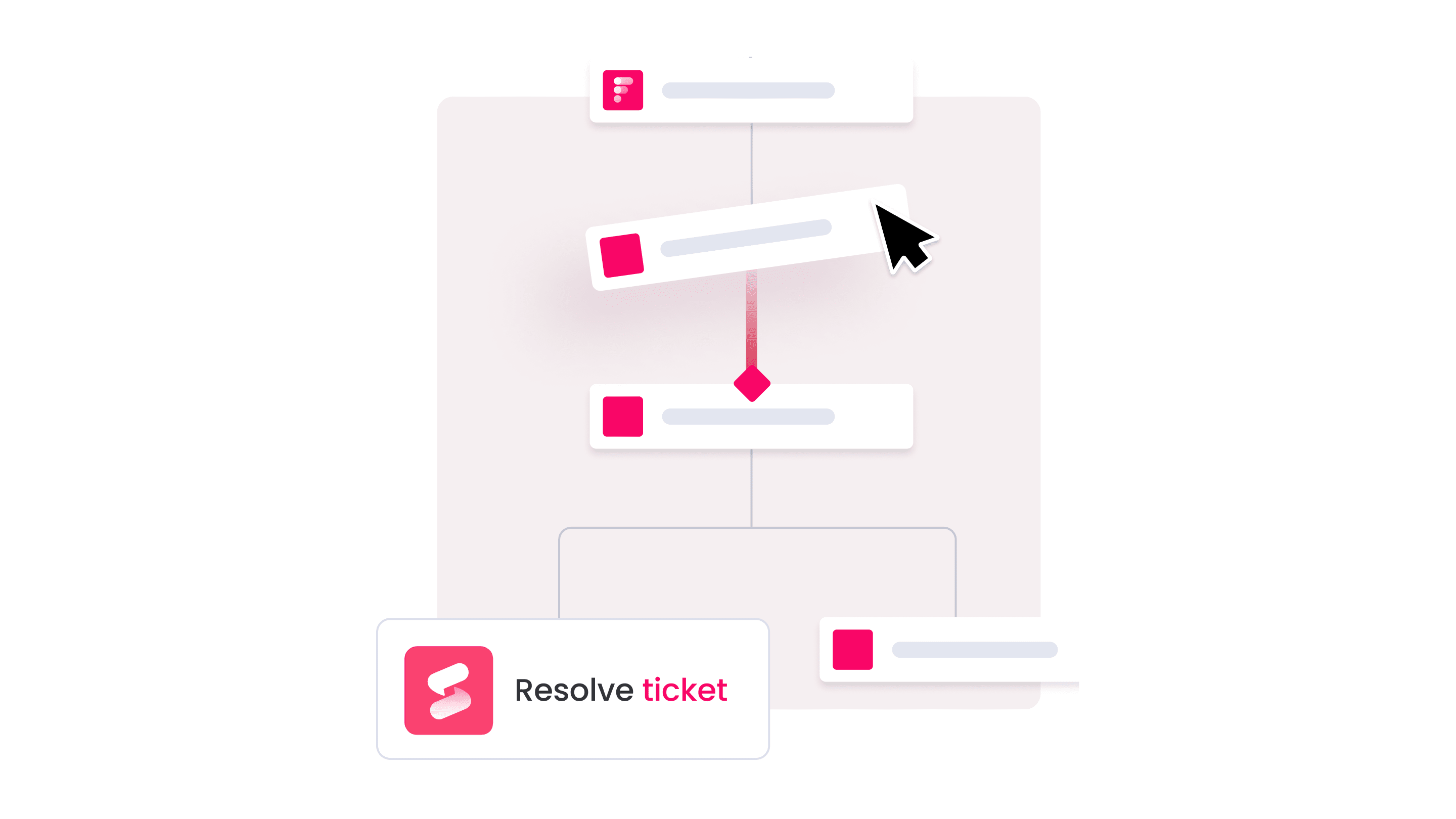
Understanding the CMDB in ITIL
The Configuration Management Database (CMDB) is where all your configuration data lives. While configuration management is the practice, the CMDB is the actual database that stores the information.
The critical point is this: a CMDB is not merely a static spreadsheet, but a dynamic system that tracks component relationships and dependency mappings.
What is a configuration management database?
A CMDB is a centralized repository that stores information about all your configuration items and how they relate to each other. It’s part of a larger Configuration Management System (CMS) that includes all the processes and governance around managing this data.
The database contains detailed records for each CI, including version numbers, owners, locations, and current status. More importantly, it maps out dependencies: showing you exactly what will be affected if something changes or fails.
CMDB architecture and components
A modern CMDB consists of several key elements that work together. You’ll find CI records with detailed attributes, relationship mappings that show dependencies, and validation rules that keep data accurate.
The architecture also includes:
- Discovery engines: automatically detect changes in your environment.
- Integration points: connect with other IT management platforms.
- Data validation: ensure information stays accurate over time.
Maintaining CMDB accuracy
Maintaining data accuracy represents the biggest challenge for any CMDB. Given that the IT environment changes constantly, manual updates cannot keep pace, particularly as cloud management grows more complex.
Successful organizations use automated discovery platforms, regular audits, and clear ownership rules. Advanced solutions like monday service help by automatically updating configuration data as changes occur, reducing the manual effort required to maintain accuracy.
Core principles of ITIL configuration management
Effective configuration management follows several core principles. Understanding these helps you build a system that actually works in practice, not just in theory.
- Service asset control: configuration management gives you control over all assets that support service delivery. This aligns with IT asset management best practices by ensuring you know exactly what you own, where it’s located, and who’s responsible for it, helping to reduce security risks and manage assets proactively.
- Configuration verification: regular verification ensures your CMDB matches reality, as configuration data naturally drifts over time (e.g., servers moved, software updated). Verification activities compare your records against the actual environment, using a mix of automated checks and manual review for critical components.
- Relationship management: understanding relationships between CIs is just as important as tracking the items themselves. These relationships (e.g., a database supporting many applications) enable impact analysis and better decision-making. Platforms like monday service visualize these connections through intuitive dashboards, making complex dependencies easy to understand.
- Information security: configuration management supports security by maintaining records of authorized configurations. This allows for immediate detection of unauthorized changes, tracking baseline configurations, and controlling who can access and modify configuration data.
Configuration management process: key stages
The configuration management process follows a structured approach that ensures nothing falls through the cracks. Each phase builds on the previous one to create a comprehensive system.
1. Planning and design
Success starts with good planning. You need to define what’s in scope, establish naming conventions, and design your CMDB structure.
Key planning decisions include:
- Scope definition: which CIs will you track?
- Categorization: how will you group similar items?
- Naming standards: what conventions will you use?
- Access controls: who can view and modify data?
2. Identification and control
Once planning is complete, you start identifying and registering CIs. Each item gets a unique identifier and goes under version control.
Configuration baselines establish your approved configurations. These serve as reference points for detecting unauthorized changes and planning updates.
3. Status accounting
Every CI has a lifecycle status: under development, live, under maintenance, or retired. Tracking these statuses helps you understand your environment’s current state.
This information supports better decision-making. This ensures you can confidently direct resources to active systems while keeping track of components still in development.
4. Verification and audit
Regular audits ensure your CMDB stays accurate. Different audit types serve different purposes:
- Routine checks: validate data accuracy.
- Compliance audits: ensure regulatory requirements are met.
- Full audits: comprehensive review of all configuration data.
Benefits of implementing configuration management
When done right, configuration management delivers real business value. The benefits extend far beyond IT too, impacting service quality, risk management, and operational costs.
Enhanced service visibility
Configuration management gives you complete visibility into your IT infrastructure. You can see how components work together and identify potential issues before they cause problems.
This visibility improves communication with business stakeholders. When they ask about service dependencies or potential impacts, you have immediate answers backed by accurate data.
Increased service reliability
Accurate configuration data prevents outages by enabling thorough impact analysis. Before making changes, you know exactly what might be affected.
During incidents, configuration data speeds up resolution. Research reveals that formal processes built on this data can reduce incident resolution time by up to 50%, as teams can quickly identify affected systems and understand dependencies.
Improved change success rates
Understanding your current environment dramatically improves change success. You can identify conflicts, plan sequences, and prepare rollbacks based on real data.
Organizations with mature configuration management achieve higher change success rates and greater stability, demonstrating how it underpins effective ITSM processes. monday service enhances this by connecting configuration data directly to change workflows.
Stronger compliance and governance
Many regulations require accurate IT asset inventories and change control processes. Configuration management provides the documentation and audit trails you need.
The practice also supports internal governance by demonstrating control over IT assets and providing clear accountability for changes.
5 best practices for ITIL configuration management
These proven practices help you avoid common pitfalls and build a sustainable configuration management system.
1. Implement automated discovery
Manual data collection can’t scale with modern IT environments. Automated discovery continuously scans for new components and changes.
Choose platforms that cover all your component types and integrate with existing systems. The goal is comprehensive coverage without manual intervention.
2. Establish clear data governance
Define who owns configuration data, how it gets updated, and what quality standards apply. Without clear governance, even the best technical implementation fails.
Key governance elements include:
- Data ownership: who’s responsible for accuracy?
- Update procedures: how do changes get approved?
- Quality metrics: how do you measure success?
3. Define configuration baselines
Baselines represent your approved configurations. They help detect unauthorized changes and ensure components stay in compliance.
Review baselines regularly to keep them current. What worked last year might not meet today’s security or performance requirements.
4. Regular configuration audits
Schedule different audit types based on component criticality. High-risk systems need frequent checks, while stable components can be reviewed less often.
Use audit results to improve your processes. If you keep finding the same issues, address the root cause rather than just fixing symptoms.
5. Integrate with ITSM processes
Configuration management works best when integrated with other ITIL practices. Change management needs impact analysis. Incident management needs dependency information.
Solutions like monday service excel here by providing a unified platform where all these processes connect naturally. Configuration data flows seamlessly into tickets, changes, and problems.
"Our team LOVES the monday service platform and we’re already exploring how we could incorporate it for other departments, too. It has streamlined our workflow in a way that both our team and customers appreciate."
Andrew Marshall | VP Operations
״monday service provides clear insights into requests volume and types, response times, and trends - helping us continuously improve operations"
Grant De Waal-Dubla | CIO"The biggest value for us is speed and flexibility. You can get up and running in days, change anything instantly, and see everything in real time. And you don’t need a dedicated admin to do it."
Clive Camilleri | Head of People Tech & OperationsConfiguration management vs IT asset management
Many people confuse these two practices. While they overlap, they serve different purposes and focus on different aspects of IT management.
Key differences
Configuration management focuses on service delivery: how components work together to provide business value. IT asset management focuses on financial aspects like procurement, depreciation, and asset lifecycle management.
The data reflects these different goals:
- Configuration management tracks: technical attributes, relationships, service impact.
- Asset management tracks: purchase dates, costs, contracts, warranties.
When to use each approach
Prioritize configuration management when service quality and operational efficiency matter most. You need to understand dependencies and manage changes effectively.
Choose asset management when financial optimization is key. You’re tracking total cost of ownership and managing vendor relationships.
Integration opportunities
These practices complement each other. Configuration management tells you how things work together. Asset management tells you what they cost.
Flexible platforms like monday service support both approaches through flexible data models. Start with one and expand as needed.
Integrating configuration management with other ITIL practices
Configuration management multiplies its value when integrated with other ITIL practices. Each integration point below should be looked at carefully as it creates new opportunities for efficiency and risk reduction.
Change enablement
Configuration data transforms change planning. Instead of guessing about impacts, you see exactly what connects to what.
Impact analysis becomes precise and comprehensive: you identify all affected components and plan your approach accordingly.
Incident management
During incidents, every second counts. Configuration data accelerates diagnosis by showing you system dependencies and recent changes.
Teams quickly understand the scope of impact and identify potential causes, which is crucial for ITSM knowledge management. What might take hours of investigation happens in minutes.
Problem management
Root cause analysis depends on understanding system relationships. Configuration data reveals patterns that might otherwise go unnoticed.
You can trace issues across seemingly unrelated systems and identify the true source of recurring problems.
Release management
Successful releases require accurate environment information. Configuration management provides the blueprint for deployment planning.
Post-release verification becomes straightforward when you can compare actual configurations against planned states.
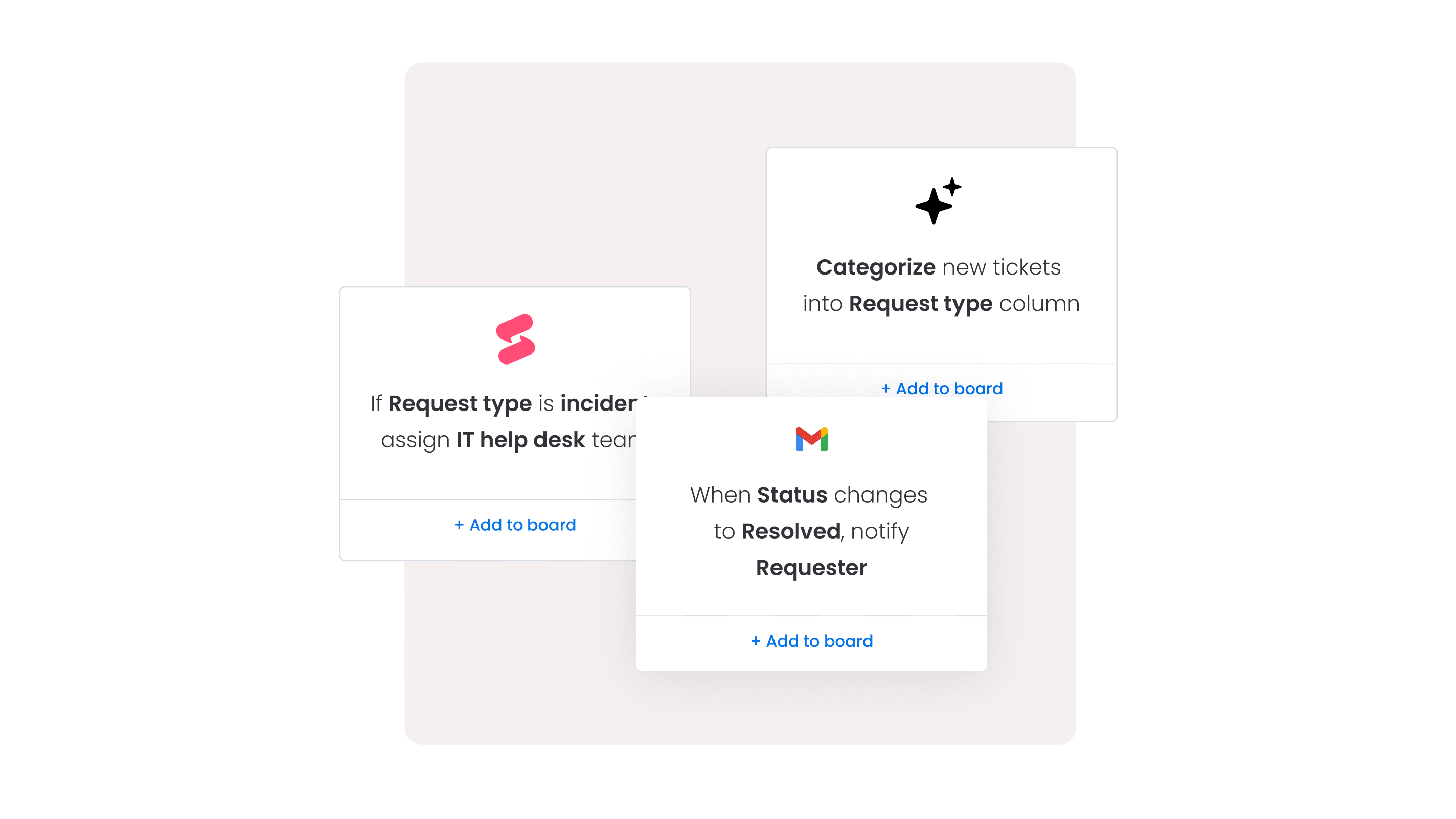
Modern approaches to configuration management
Technology keeps evolving, and configuration management evolves with it. Modern approaches address traditional limitations while adding new capabilities.
AI and machine learning applications
AI transforms configuration management through pattern recognition and predictive analytics. Machine learning identifies configuration drift and predicts potential failures.
Practical applications include:
- Automated categorization: AI classifies new CIs based on attributes.
- Anomaly detection: spot unusual changes before they cause problems.
- Predictive maintenance: identify components likely to fail.
Cloud configuration management
Cloud environments change constantly. Auto-scaling, containers, and infrastructure-as-code create new challenges for configuration tracking.
Modern platforms adapt by using APIs and cloud-native monitoring. They track ephemeral resources and maintain accuracy despite constant change.
Real-time configuration monitoring
Traditional periodic scans create dangerous gaps. Real-time monitoring captures changes as they happen.
This immediate visibility enables faster response to issues and more accurate decision-making. You work with current data, not yesterday’s snapshot.
How monday service transforms configuration management
A strong configuration management practice only works when teams can actually use the data. That’s where the right platform makes a difference. Instead of relying on manual updates or scattered tools, monday service brings your configuration information into one connected workspace, making it easier to maintain accuracy, understand dependencies, and act on insights in real time.
AI-powered configuration discovery
monday service uses AI to automatically discover and classify configuration items. The system learns from your patterns and improves accuracy over time.
This automation dramatically reduces the manual effort traditionally required for CMDB maintenance. Your team focuses on using the data, not collecting it.
Visual dependency mapping
Complex relationships become clear through visual mapping. See how components connect and understand impacts at a glance.
These visual tools help you communicate effectively with stakeholders who might not understand technical diagrams. Everyone can see and understand service dependencies.
Automated workflow integration
Configuration data flows seamlessly into your service management workflows. When handling incidents or planning changes, relevant configuration information appears automatically.
This integration eliminates the need for separate lookups or manual data entry. Everything you need is right where you need it.
No-code customization
Adapt monday service to your specific needs without writing code. The platform’s flexibility means you can start simple and evolve as requirements change.
This approach reduces implementation time and ongoing maintenance costs: you control your configuration management destiny without depending on developers.
Frequently asked questions
What are the 5 stages of ITIL configuration management?
The 5 stages of ITIL configuration management are planning and design, identification and control, status accounting, verification and audit, and continual improvement. These stages create a complete lifecycle for managing configuration items from initial identification through retirement and ongoing optimization.
What are the main components of a configuration management database?
A configuration management database contains four main components: configuration item records with detailed information, attributes describing each item's characteristics, relationship mappings showing dependencies, and status tracking throughout the lifecycle. These elements work together to provide comprehensive infrastructure visibility.
How does configuration management differ from asset management?
Configuration management differs from asset management by focusing on technical relationships and service delivery rather than financial tracking. While asset management handles procurement and costs, configuration management tracks how components work together to deliver services.
What types of items should be included as configuration items?
Configuration items should include hardware like servers and network devices, software including applications and operating systems, documentation such as process guides, and key personnel with critical access or knowledge. Include any component that impacts service delivery or requires management oversight.
How often should configuration audits be performed?
Configuration audits should happen monthly for high-change critical systems, quarterly for moderate-change environments, and annually for stable systems. The frequency depends on how often your environment changes and how critical accuracy is for your operations.
What are the biggest challenges in implementing configuration management?
The biggest challenges in implementing configuration management are maintaining data accuracy as environments change, getting buy-in from stakeholders across departments, and integrating with existing processes and platforms. Success requires strong governance and automated discovery capabilities.
