Whether launching a new product, managing a complex portfolio, or scaling operations, risks have a way of creeping in and throwing things off track. It pays to know what’s coming up, so you have a chance to create a response plan to deal with these threats.
Risk identification enables you to spot vulnerabilities early. When the process works well, you can take proactive action before problems turn into delays, cost overruns, or compliance failures. This guide walks you through 7 steps to identify risks and overcome some common challenges.
Get StartedWhat is risk identification?
Risk identification is the process of finding and documenting any risks that prevent a team or organization from achieving its goals. This identification is the first step in the overarching risk management process — a broader set of steps involved in developing and implementing strategies to overcome the risks you’ve identified.
For example, a company expanding into new markets might identify currency fluctuations and local regulations as key risks before launch. From here, they would attempt to mitigate these risks by locking in favorable exchange rates or consulting local legal experts to keep the rollout on track.
Why risk identification matters
Risk identification plays a foundational role in organizational performance, but it requires resources and commitment to achieve results for your business. Here are the specific benefits you can expect when you invest in risk identification.
Avoid costly disruptions
Project success hinges on thoughtful planning to reach every milestone on time and cross the finish line within budget. Yet, missed deadlines and budget overruns remain persistent issues in project delivery. According to Wellingtone’s State of Project Management research, only 34% of organizations report that they “mostly” or “always” complete projects on time. And the same percentage stays within budget.
Unexpected risks contribute to this gap between planning and execution. But when teams take the time to identify potential threats at the outset, whether related to scope, vendors, dependencies, or regulatory shifts, they’re better positioned to reduce delays, avoid rework, and maintain delivery standards across the board.
When risk identification is done right, it doesn’t just feel like smart planning — it shows up in performance. Teams that consistently flag risks early report fewer missed milestones, reduced rework, and tighter budget adherence. Tracking metrics like number of risks mitigated pre-impact, reduction in time lost to delays, or register refresh rate can help quantify your team’s progress over time.
Support effective resource allocation
Resource allocation decisions can fail if teams don’t spot risks early enough to shift direction.
In McKinsey’s 2024 global survey, just 53% of executives said their organizations consistently fund their top strategic priorities. This kind of misalignment typically stems from hidden capacity constraints, underappreciated cost risks, or competing initiatives that pull focus.
Identifying those risks upfront gives leaders the visibility they need to allocate time, talent, and budget more effectively, long before locking resources into the wrong priorities.
Encourage cross-functional transparency
Risk exposure isn’t isolated to a single function or team. So businesses must coordinate across departments to notice or address key threats before they affect broader outcomes.
When risk identification is part of cross-functional planning, it creates space for more open conversations around dependencies, constraints, and assumptions. This shift supports better alignment, reduces duplication of effort, and acknowledges risks at the right levels of the organization.
Strengthen organizational agility
Organizations that recognize and plan for potential risks are often more capable of adapting when change is required. Our World of Work Report highlights this connection: while the tech sector experienced the most organizational change in 2024, it also reported the strongest confidence in how those changes were handled.
The data suggests a clear correlation between preparedness and performance. In environments where teams have anticipated potential disruptions, such as new software rollouts, role changes, or restructuring, employees are more likely to view change as manageable rather than overwhelming. Risk identification establishes that readiness, contributing to a more resilient, agile workplace culture.
The risk identification process: 7 steps to uncover, understand, and prioritize risks
Here’s a structured, repeatable process that goes beyond checklists to proactively uncover risk in your organization. This process works across use cases, from enterprise-wide planning to targeted project risk identification.
1. Establish context and boundaries
Before identifying risks, clarify what you’re protecting. This starts with defining the scope and success criteria of the initiative, whether a project, program, process, or business unit. Get alignment about:
- Objectives, deliverables, and success metrics
- Internal and external factors influencing risk (e.g., regulatory, market, operational)
- Risk appetite or tolerance levels
2. Engage stakeholders across the business
A comprehensive identification process should blast through organizational silos by involving a wide range of stakeholders. Expose risks that might otherwise be overlooked by including a range of diverse voices from:
- Project sponsors and executive leadership
- Operational and functional teams, such as finance, legal, compliance, and IT
- End users and customer-facing teams
- External vendors, vendors, or advisors where relevant
Obtaining cross-functional input gives teams a clearer picture of risk exposure and makes it easier to assign ownership early. Using tools like the RACI model can clarify who’s responsible for identifying, monitoring, or addressing different risk types.
3. Gather and analyze relevant data
Meaningful risk identification should be data-informed. This goes beyond “what could go wrong” to include historical evidence and forward-looking indicators. To find this crucial evidence, pull data from:
- Past project retrospectives or audits
- Industry and regulatory benchmarks
- Customer feedback, complaints, or service tickets
- External sources such as market trend reports or competitor activity
4. Choose the right risk identification methodology
Not every risk identification method suits every project. A high-level strategy refresh requires a different approach than a time-sensitive product launch or a regulated infrastructure project. That’s why choosing the right method, or combination of methods, is a critical step in the process. Consider the following when choosing the right method:
- Project complexity
- Organizational maturity
- Type of risk exposure
For example, you may want to use one of the following methodologies:
- Brainstorming for simple initiatives
- Scenario planning or root cause analysis for complex projects
- Taxonomies or historical risk data in mature environments
- Facilitator-led workshops for team-based discovery
- SWOT analysis or benchmarking for strategic risk
- Root cause analysis to recurring operational issues
There’s no one-size-fits-all approach. The key is to select methods that give you depth without overcomplicating the process.
5. Categorize and connect risks
Grouping risks can clarify patterns, identify systemic issues, and make threats more digestible for stakeholders. You might categorize risks by:
- Risk type (e.g., strategic, financial, compliance, reputational)
- Business impact area (e.g., revenue, timeline, customer trust, legal)
- Source of risk (internal or external)
From here, map the interdependencies between risks, such as one risk triggering others. This approach reveals critical points of failure or concentration risks.
6. Estimate probability and impact
After risk determination, business leaders want to know “if” the risk will happen and how bad the fallout could be. This step is an initial evaluation that determines which risks are worth deeper analysis or immediate mitigation planning. You might use one of the following common approaches:
- Qualitative scales (e.g., high/medium/low)
- Risk matrices plotting likelihood vs. impact
- Early-stage scoring or ranking models
Once you’ve estimated likelihood and impact, the next step is to decide which risks require immediate attention. Prioritizing risks at this stage helps teams focus mitigation efforts where they’ll have the greatest impact.
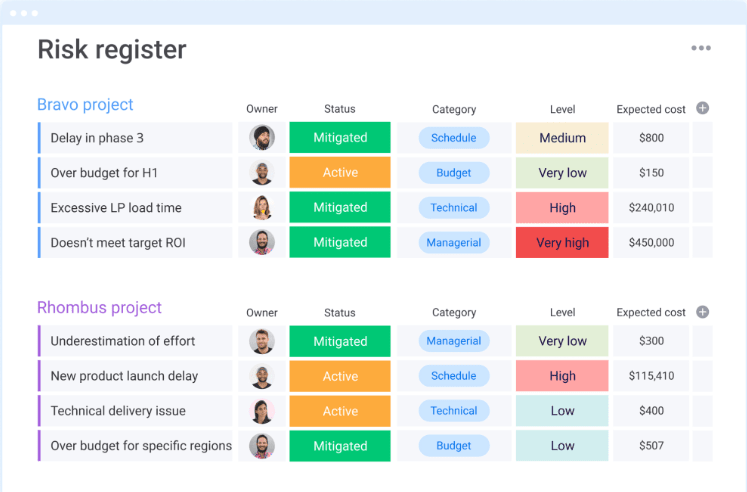
7. Document risks in a central register
Record all identified risks in a structured, dynamic format that’s accessible to the right people and regularly maintained. Include a clear risk statement for each entry to define the scope and context of the risk in more detail, including:
- Risk name and clear description
- Category and related business objective
- Identified source and trigger
- Likelihood and impact estimates
- Assigned owner
- Status and notes on mitigation plans
Essential tools to streamline risk identification
Risk identification can easily become fragmented or limited in scope, especially in complex environments. To make the process more effective and scalable, high-performing teams rely on a mix of risk identification techniques that support real-time visibility and collaboration.
Risk management platforms
Spreadsheets and siloed documentation often result in version control issues, delays, and limited visibility. Risk management platforms solve this by offering a unified system where teams can capture, track, and act on risks in real time. With the right tools, teams can:
- Set up customizable risk boards tailored to any project or department.
- Automate assignments, notifications, and escalations to ensure accountability.
- Visualize risk exposure across portfolios with dashboards.
- Pull in data from integrated tools like Jira, Salesforce, or Slack.
- Access AI-powered insights that flag high-risk areas based on historical trends.
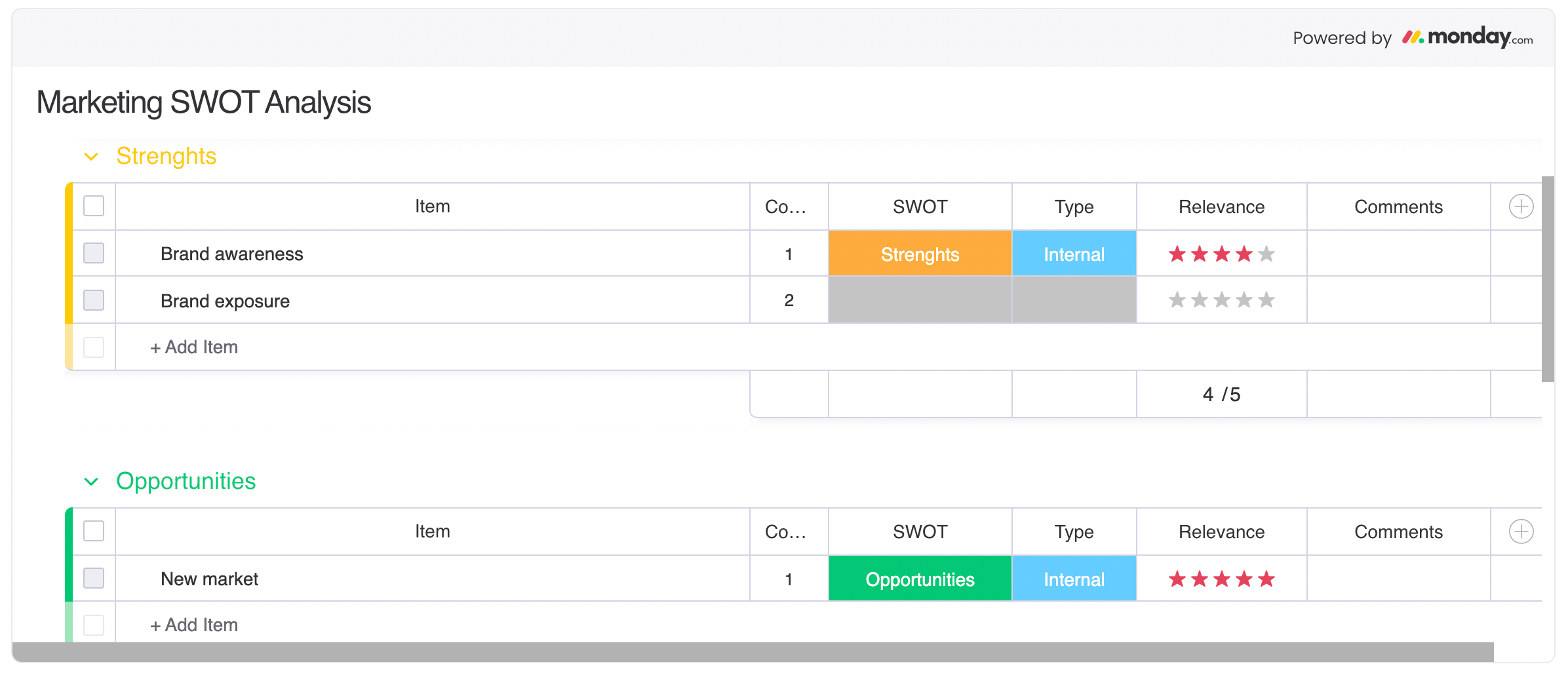
SWOT analysis
A SWOT analysis is a structured technique used to evaluate four key dimensions of a business or project environment: Strengths, Weaknesses, Opportunities, and Threats. Businesses often run the analysis during planning and strategic alignment, but it’s also highly effective in identifying risks from both internal and external sources. Here’s how each part of the framework can surface potential risks:
- Strengths aren’t typically associated with risk, but over-reliance on a single strength (e.g., a key vendor or technology) may present a vulnerability.
- Weaknesses reveal internal limitations that could hinder progress, such as skill gaps, outdated systems, or inconsistent processes.
- Opportunities can also carry risk, particularly if they require aggressive investment, resource reallocation, or rapid change.
- Threats point to external pressures like market competition, regulatory changes, or geopolitical instability.
Risk brainstorming sessions
Open brainstorming sessions can spot risks that may not show up in systems or historical data. This technique reinforces a culture where identifying risks is seen as a proactive strength, not a sign of pessimism or overcaution.
When well-run, these sessions capture real-world concerns from multiple perspectives and often reveal operational blind spots. To improve the quality of insights:
- Appoint a facilitator to keep the conversation focused and balanced.
- Provide context ahead of time, including your scope and success metrics.
- Encourage contributions from departments that typically operate outside of formal risk discussions, like marketing, support, or logistics.
- Group your responses into themes or risk categories as part of the documentation process.
Root cause analysis
When risks stem from repeatable issues or chronic process failures, surface-level fixes rarely prevent recurrence. Root cause analysis gives teams a structured way to investigate what’s really driving potential problems and identify risks before they create damage. Here are some approaches:
- Use the “5 Whys” technique to repeatedly drill into cause-and-effect sequences by asking why.
- Create cause-and-effect diagrams (also known as Ishikawa or fishbone diagrams) to visualize contributing factors.
- Look for patterns across multiple teams or workflows that point to shared weaknesses.
- Involve operational leads who understand the full lifecycle of a process.
The outcome is a deeper understanding of the systems and behaviors that create risk in the first place.
3 risk identification examples in the real world
Risk identification comes to life in the real world when organizations anticipate what could go wrong before it does, sometimes protecting millions in assets, reputation, or operational continuity. Below are 3 examples of risk identification and management in action.
1. Supply chain disruption: GM identifies risk in EV battery material dependency
As General Motors (GM) aggressively scales its electric vehicle (EV) production, it requires a strategy to source a stable and predictable supply of critical raw materials such as graphite, used in battery anodes.
Risk identified: As far back as 2019, GM flagged a strategic vulnerability in its supply chain due to heavy reliance on international sources for EV battery components. The company identified geopolitical instability, rising material costs, and regulatory risks as potential disruptors.
Impact: To mitigate this risk, GM has invested $150 million in Nouveau Monde Graphite, a Canadian mining company. The move has given GM greater supply control within North America and reduced risk exposure in its long-term electrification strategy.
2. Data security threat: Change Healthcare’s ransomware attack
Change Healthcare, a subsidiary of UnitedHealth Group, is a leading provider of healthcare technology solutions, processing 15 billion healthcare transactions annually and touching 1 in every 3 patient records in the United States.
Risk identified: In February 2024, the company detected a ransomware deployment already in progress that would go on to severely disrupt U.S. healthcare operations. The incident exposed a critical risk: vulnerabilities in core systems that may not have been fully assessed or prioritized despite the company’s scale and sensitivity of data.
Impact: The cyberattack disrupted healthcare operations on a national scale, endangering patients’ access to care, affecting critical clinical and eligibility operations, and threatening the solvency of healthcare providers. The attack also shed light on the need for earlier identification of gaps in infrastructure, legacy system dependencies, and third-party access points that can be exploited at scale.
3. Executive security: High-profile threats prompt safeguarding measures
In December 2024, Brian Thompson, CEO of UnitedHealthcare, was tragically killed in a targeted attack, highlighting growing concerns about personal security risks for high-profile executives.
Risk identified: Prior to the attack, industry analysts and corporate security experts had already flagged a growing risk tied to executive visibility. As public sentiment toward healthcare costs intensified, companies began reviewing exposure points, including open access to executive names, photos, and locations and identified a need for enhanced monitoring and protective measures.
Impact: Following the incident, major healthcare companies such as UnitedHealth Group and CVS Health quickly removed executive headshots and personal bios from public websites. Many also escalated internal risk assessments and expanded personal protection protocols for key leadership. This shift marked a broader recognition that reputational and physical risk to executives isn’t hypothetical and must be addressed through early identification and preventive strategy.
3 common risk identification mistakes
Even teams with a solid framework in place can miss the mark if the process becomes too narrow, static, or disconnected from day-to-day operations. Here are 3 common reasons risk identification efforts fall short.
Narrow scope
Focusing too narrowly on technical or immediate risk, like timeline slippage or vendor delays, often leaves broader organizational threats unaddressed. Risks related to compliance, stakeholder resistance, interdependencies, or market conditions can fly under the radar if teams only scan for what’s in front of them.
What to do instead: Start each risk identification cycle by aligning on broader business objectives and current operating conditions. Look beyond your immediate team or timeline to consider how risks could be introduced by earlier dependencies or how they might affect later phases or other departments. Revisit the full context regularly to catch changes that could shift your risk landscape.
Limited perspectives
Risk identification efforts that exclude voices from certain departments, regions, or roles can overlook critical insights. Operational staff may flag practical barriers that executives overlook. And at the top of the tree, leadership may spot strategic threats that aren’t visible to delivery teams.
What to do instead: Involve a mix of stakeholders, including frontline team members, partners, and compliance or legal teams. To gain their insights, use structured input methods like risk workshops or surveys to capture various perspectives and explain to participants how you plan to use their input.
Inconsistent updates
Treating risk identification as a one-time task leads to outdated records, missed emerging risks, and a lack of opportunities to course-correct early. This is especially common when teams complete initial assessments at kickoff and never revisit them.
What to do instead: Build risk reviews into project milestones, quarterly planning cycles, or portfolio health checks. Make it part of your team’s operating rhythm to revisit risk registers, reprioritize threats, and add new ones as context shifts, whether due to internal changes or external forces.
Identify risks automatically with monday work management risk register
Risk identification should never feel like a reactive process. With the right systems in place, teams can confidently reveal potential challenges, collaborate across departments, and keep key initiatives moving forward — even in complex environments.
Teams can use monday work management as a unified workspace to turn risk awareness into everyday practice. Here’s how to build a process that feels less like risk control and more like risk confidence.
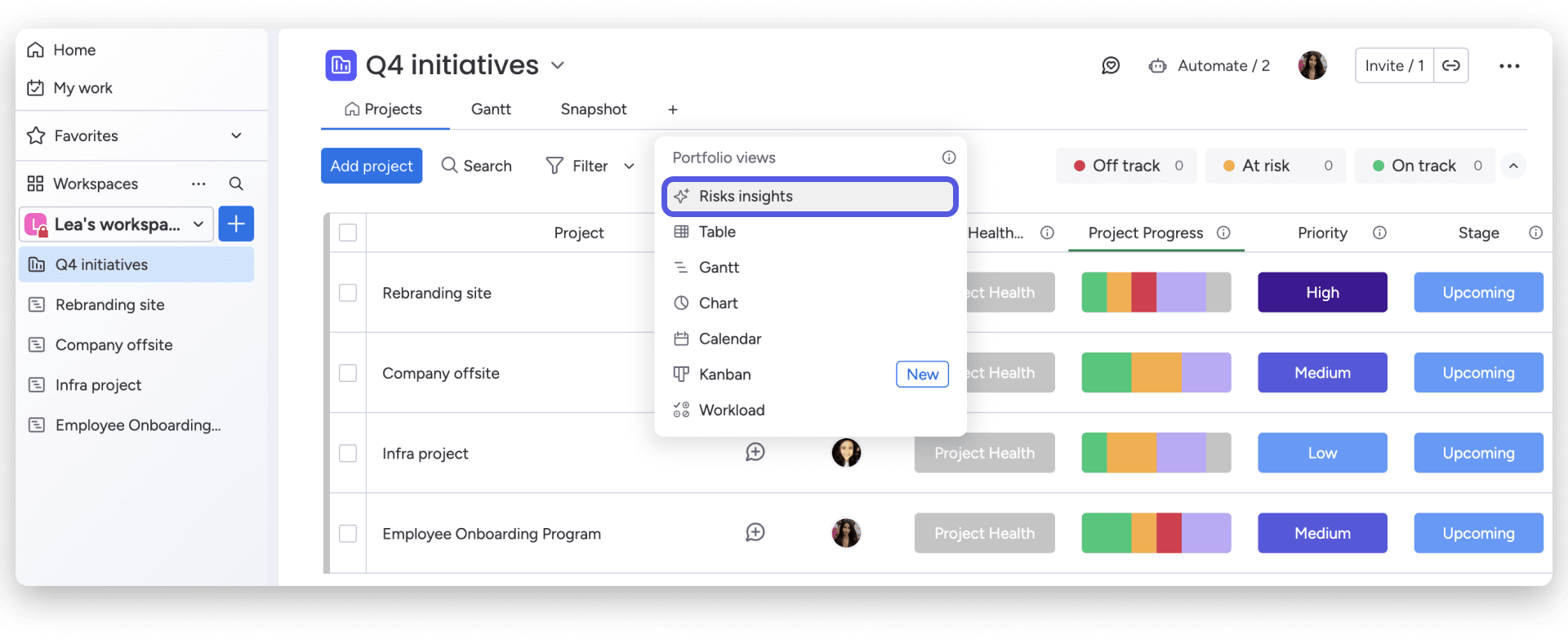
Surface potential risks
The earlier you spot potential issues, the more options you have to respond with focus and clarity. That’s where monday AI’s Portfolio Risk Insights can help. Think of it as a second set of eyes — one that scans for risk across timelines, boards, and updates, flagging issues even when your team’s too busy to notice them.
This feature automatically scans project boards across your portfolio, flagging items that may need attention based on signals like item names, updates, and activity history. You’ll receive a daily view of risk levels across your projects, helping you prioritize with purpose and stay ahead of blockers before they slow down delivery.
Filter by severity, review individual risks in context, notify project owners, or generate a summary report, all from one intuitive view.
Build your risk register
Risk identification is more manageable when your insights live in one place. A centralized risk register helps teams document, organize, and take ownership of potential challenges, without relying on spreadsheets or disconnected notes
With monday work management, you can build a fully tailored risk register that fits your organization’s structure. Add fields that matter to your process, like risk type, owner, likelihood, impact, and mitigation plans, and keep everything linked to the initiatives or timelines it affects. This keeps your risk data connected, current, and easy to act on.
Collaborate with key stakeholders
Clear communication makes all the difference when identifying and responding to risk. With monday work management’s collaborative boards and dashboards, teams can stay aligned and responsive without needing extra meetings or long email threads.
Comment directly on risk items, update statuses, tag team members, and pull in cross-functional views, all within the same workspace. The result: everyone involved in your projects can contribute meaningfully to risk planning, from strategy through execution.
Ensure enterprise-grade security
When working across departments or regions, you need a platform that protects your data while still allowing teams to move quickly. Our platform is equipped with enterprise-grade security features that support both scale and flexibility.
From role-based permissions to audit trails, encryption, and compliance with key standards like SOC 2 Type II, you can manage sensitive risk data confidently while giving the right people the access they need.

Build your risk identification process with greater clarity, collaboration, and insight — all within monday work management. Start your free trial and create a system that helps your team move forward with confidence.
Get StartedFAQs
Is a dedicated risk manager necessary for success?
No, a dedicated risk manager is not required for success, but clear ownership of the risk identification process is essential. Teams can manage risk effectively by assigning responsibility, using the right tools, and embedding risk awareness into project workflows.
Do automated tools replace face-to-face discussions?
No, automated tools support risk tracking, but they don’t replace the need for human input and team dialogue. But combining software with regular discussions can lead to more complete and actionable risk identification.
What are 5 ways to identify risks?
5 common risk identification methods include:
- Brainstorming: Gathering team input quickly by surfacing concerns in a structured, facilitator-led session
- SWOT analysis: Identifying risks through external threats or internal weaknesses uncovered during strategic planning
- Root cause analysis: Tracing potential risks back to their source by analyzing past failures or recurring issues
- Stakeholder interviews: Uncovering risks from different perspectives by speaking directly with cross-functional contributors
- Reviewing historical project data: Reviewing lessons learned from similar past initiatives to flag risks that could repeat
Using several of these methods will provide you with the best picture of the risk landscape.
What is an example of a risk identifier?
An example of a risk identifier is a missed deadline in a previous project phase. It can signal potential timeline risks in the current initiative and prompt teams to explore root causes or similar vulnerabilities.
What are the 3 stages of risk identification?
The 3 key stages of risk identification are:
- Establishing context and scope: Define what you're evaluating and the conditions that could influence risk
- Generating a list of potential risks: Use structured techniques to uncover threats from all angles
- Documenting and categorizing those risks: Record risks in a clear format and group them by type, source, or impact
 Get started
Get started 
