Protecting your business from digital threats takes more than strong defenses. It requires a coordinated response when incidents happen, connecting security alerts to clear, decisive action across your organization. When security works in sync with operations, you build resilience that goes beyond blocking attacks.
This article covers the essential IT security solutions every business needs — from network and cloud security to identity and data protection — and how AI helps detect threats and automate responses.
You’ll also learn how to create a clear framework with a service management solution like monday service for both protection and response, so you can stay compliant, reduce risk, and act quickly when it matters most.
Key takeaways
- Every business needs multiple security layers: Network, endpoint, cloud, data, identity, and application security solutions work together to protect your entire organization from cyber threats.
- AI-powered security solutions detect and stop threats in real-time: Modern platforms learn attack patterns and automatically update defenses without manual intervention, catching threats before damage occurs.
- monday service streamlines security incident response: AI automatically routes security alerts to the right teams, tracks resolution progress, and integrates with your existing security platforms for faster recovery.
- Start with a security assessment to identify gaps: Evaluate current platforms, map critical assets, and define requirements before selecting solutions that scale with your business growth.
- Security failures shut down operations and destroy trust: Without proper protection, a single breach can halt business operations, trigger compliance penalties, and damage your reputation for years.
What are IT security solutions?
IT security solutions are technologies and platforms that protect your organization’s digital assets, networks, and data from cyber threats. This means they create multiple layers of defense against attacks like malware, ransomware, and unauthorized access attempts.
Think of IT security solutions as your digital security team — they work around the clock to monitor, detect, and respond to threats before they can damage your business. Unlike basic antivirus software that only protects individual computers, these solutions protect your entire organization, often aligning with IT service management principles to ensure consistent coverage.
Modern IT security solutions use artificial intelligence to spot threats in real-time. In fact, the 2024 Deloitte-NASCIO Cybersecurity Study found that 43 states are already using or plan to use generative AI to enhance their cybersecurity posture within the next year.
Why every business needs IT security solutions
Your business runs on digital systems — from email and customer databases to financial records and intellectual property. Implementing a secure customer portal and other solutions ensures you’re not leaving the front door wide open for attackers.
Rising cyber threats target organizations of all sizes
Cybercriminals don’t just target big corporations anymore. Small and medium businesses are equally attractive targets because they often have fewer security resources, making enterprise service management crucial for unified protection. Here’s what you’re up against:
- Ransomware attacks: Malicious software that locks your files until you pay a ransom
- Phishing campaigns: Fake emails designed to trick employees into revealing passwords or sensitive data. In the third quarter of 2024, business email compromise (BEC) scams surged, accounting for 58% of phishing attempts.
- Insider threats: Security risks from employees or contractors who have legitimate system access
These threats change constantly. What protected your organization last year might not work today, which is why you need security solutions that adapt as quickly as attackers do.
Compliance standards require comprehensive security
If you handle customer data, healthcare records, or financial information, you’re legally required to protect it. Regulations like GDPR, HIPAA, and SOX come with strict security requirements and hefty penalties for non-compliance.
IT security solutions help you meet these requirements automatically. They track who accesses what data, generate compliance reports, and ensure you’re following the rules — without you having to become a legal expert, making service management key to seamless regulatory adherence.
Business operations depend on a secure infrastructure
When security fails, everything stops. A single breach can shut down your operations, destroy customer trust, and damage your reputation for years. But with proper security solutions in place, you can operate confidently knowing your business is protected.
AI help desk software like monday service helps organizations coordinate their security response efforts across departments, ensuring faster recovery when incidents do occur. Additionally, these AI automations can handle routine incident inquiries, allowing security teams to focus on critical initiatives.
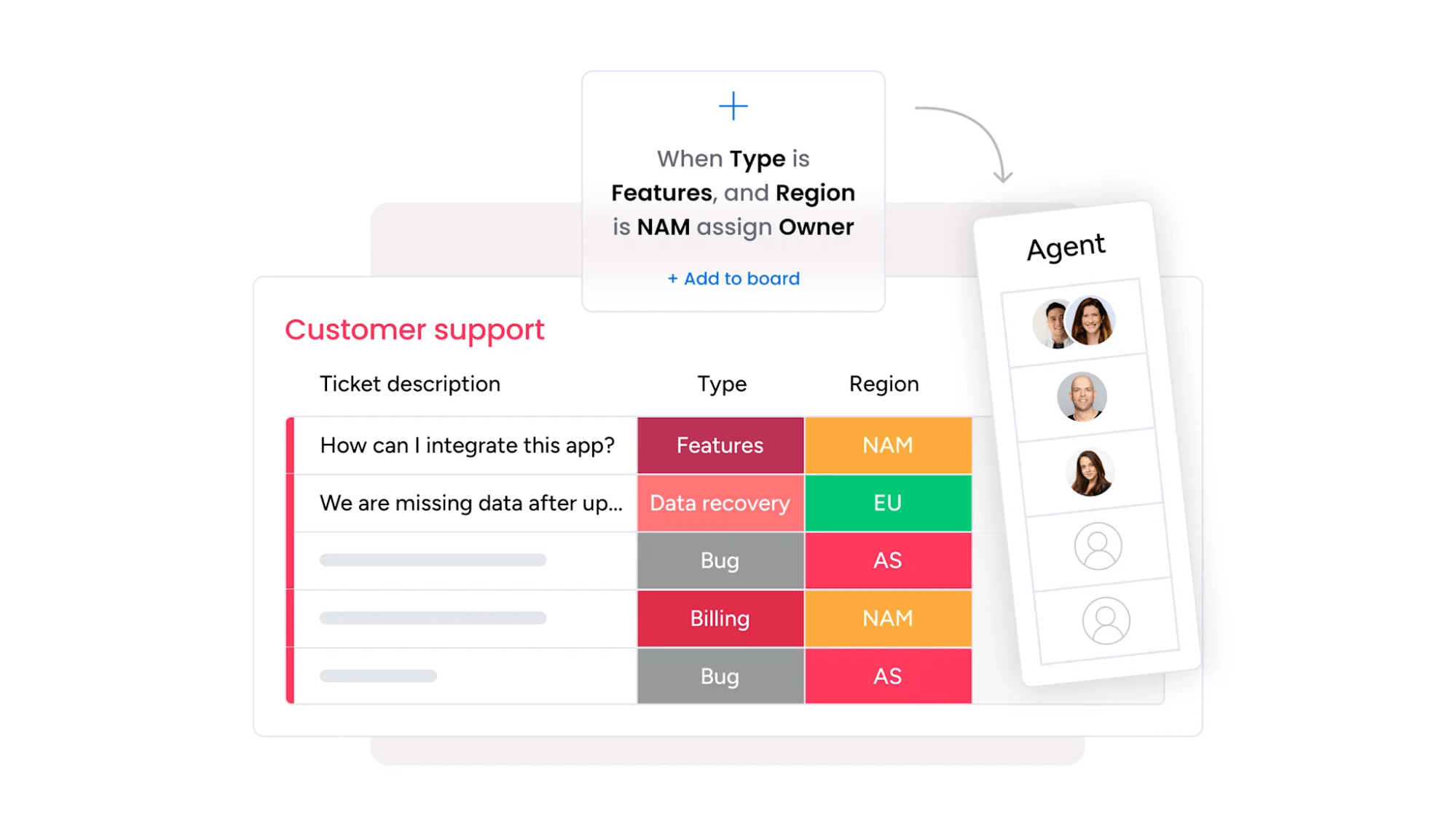
6 types of IT security solutions every organization needs
Building effective security means understanding which solutions protect against specific threats. Each type serves a unique purpose in your overall defense strategy, and choosing the right service management platform can help you find the perfect fit for your organization’s unique security needs.
1. Network security solutions
Network security solutions protect data as it moves through your organization. They act like security checkpoints, monitoring all traffic and blocking anything suspicious.
These solutions include firewalls that block unauthorized access, intrusion detection systems that spot unusual activity, and network segmentation that keeps sensitive areas separate from general traffic. When threats are detected, they trigger immediate alerts and can automatically block malicious traffic.
2. Endpoint security solutions
Every device connected to your network — laptops, phones, tablets, even printers — is a potential entry point for attackers. Endpoint security solutions protect these devices from malware and unauthorized access.
Modern endpoint protection goes beyond traditional antivirus. It watches how programs behave, spots suspicious patterns, and can isolate infected devices before threats spread across your network.
3. Cloud security solutions
More businesses store data and run applications in the cloud, which creates new security challenges. Cloud security solutions protect your cloud-based assets with specialized platforms designed for these environments.
Key capabilities include:
- Cloud access security brokers (CASB): Monitor and control how employees use cloud applications
- Cloud security posture management (CSPM): Continuously check cloud configurations for vulnerabilities
- Data encryption: Protect information stored in cloud services
4. Data security solutions
Data security solutions focus on protecting your most valuable asset — information. Alongside these solutions, integrating AI in asset management can enhance oversight of hardware and software assets, increasing visibility into where sensitive data lives, who accesses it, and how it moves through your organization.
Data loss prevention (DLP) systems automatically identify sensitive information like credit card numbers or social security numbers. They can block unauthorized sharing and alert you when someone tries to move protected data outside your organization.
5. Identity and access management solutions
You need to know exactly who’s accessing your systems and what they’re allowed to do. Identity and access management (IAM) solutions verify user identities and control their permissions.
These platforms provide single sign-on (SSO) so employees only need one password for multiple systems. They also add multi-factor authentication (MFA) for extra security on sensitive systems, and maintain detailed logs of who accessed what and when.
6. Application security solutions
Your business applications — whether customer-facing websites or internal systems — need protection from attacks. Application security solutions defend against threats that target software vulnerabilities.
Web application firewalls (WAF) filter out malicious traffic before it reaches your applications. Security testing platforms help developers find and fix vulnerabilities before applications go live, while runtime protection guards applications while they’re running.
5 key benefits of modern IT security solutions
Investing in IT security solutions delivers concrete benefits that go beyond basic protection. Here’s what you can expect when you implement comprehensive security measures.
1. Real-time threat detection and prevention
AI-powered solutions analyze patterns across your organization to spot suspicious behavior instantly. By learning what’s normal, they flag unusual activity, surface emerging attack methods through threat intelligence feeds, and catch incidents before they escalate.
2. Automated security incident response
When every second counts, automation ensures threats are contained quickly. Security orchestration platforms can trigger response steps without waiting for manual intervention.
A platform like monday service enhances this by automatically creating incident tickets, routing them to the right teams, and tracking resolution progress — keeping recovery fast and organized. Leveraging AI service management can further streamline these processes across the entire organization.
3. Complete visibility across your IT environment
You can’t protect what you can’t see. Modern security solutions provide dashboards that show your entire security posture at a glance.
This visibility helps you:
- Spot trends: Identify patterns in attacks or vulnerabilities
- Make informed decisions: Allocate resources based on actual risk data
- Prove compliance: Generate reports showing your security measures meet regulatory requirements
4. Continuous monitoring to reduce downtime
Security monitoring never stops. Platforms like SIEM collect signals from every corner of your environment, establishing baselines for normal activity and triggering alerts when behavior deviates. This proactive approach minimizes successful breaches and limits damage when they do occur.
5. Streamlined operations and integrated workflows
Instead of juggling multiple security platforms — a growing challenge, as monday.com’s world of work report found that 57% of employees use more software than last year — integrated platforms bring everything together. Your team works from a single interface, reducing complexity and improving efficiency.
Automated reporting saves hours of manual work, while service platforms like monday service connect alerts to incident workflows. The result: faster recovery, less manual effort, and more time for strategic improvements.
IT security solutions vs cybersecurity: understanding the difference
Before choosing tools, it helps to distinguish the solutions you deploy from the broader strategy that guides them. Many people use these terms interchangeably, but understanding the difference leads to smarter decisions.
IT security solutions refer to the specific technologies and platforms you implement, including firewalls, antivirus software, monitoring systems, and more. They represent the technical layer of protection: the equipment your security team uses to detect and respond to threats.
Cybersecurity is the wider strategy. It covers how your organization approaches risk overall, including assessing vulnerabilities, creating policies, training employees, and fostering a culture of security. While IT security focuses on the tools, cybersecurity defines the governance that guides them.
Here’s the distinction at a glance:
- Definition: IT security = tools and platforms; Cybersecurity = overall strategy and practice.
- Scope: IT security = technical implementation; Cybersecurity = business strategy and risk management.
- Focus: IT security = threat detection and response; Cybersecurity = risk assessment and governance.
- Implementation: IT security = software and hardware solutions; Cybersecurity = policies, procedures, and culture.
The most effective organizations combine both strong IT security solutions and a comprehensive cybersecurity strategy. Establishing service level agreements (SLAs) with trusted providers helps ensure you have the right platforms and practices in place to stay protected.
4 steps to choose the right IT security solutions
Choosing the right security solutions takes thoughtful planning. Along the way, it’s important to define how you’ll measure performance, whether through SLAs, SLOs, or SLIs, so you know your investments are delivering. Follow these four steps to identify platforms that protect your organization without slowing down operations.
Step 1: Evaluate your current security landscape
Start by understanding what you already have. List all current security tools, identify gaps in coverage, and document recent security incidents.
Talk to teams across your organization. What security challenges do they face? Where do current solutions fall short? This assessment creates your baseline for improvement.
Step 2: Identify critical assets and vulnerabilities
Not all data and systems need the same level of protection. Identify your crown jewels — the assets that would cause the most damage if compromised.
Consider conducting vulnerability assessments to find specific weaknesses. This helps you prioritize investments where they’ll have the most impact.
Step 3: Define security requirements and budget
Balance ideal security with practical constraints. Calculate potential breach costs against security investments to build your business case.
Create clear requirements for:
- Essential capabilities: What threats must you defend against?
- Integration needs: Which existing systems must new solutions work with?
- Compliance support: What regulations must you meet?
- Scalability: How will needs change as you grow?
Step 4: Select solutions that scale with your business
Choose platforms that grow with you. Cloud-based solutions often provide the most flexibility, allowing you to add users and capabilities without major infrastructure changes.
Evaluate how potential solutions integrate with platforms like monday service for incident management. Strong integration capabilities ensure your security tools work together effectively as your needs evolve.
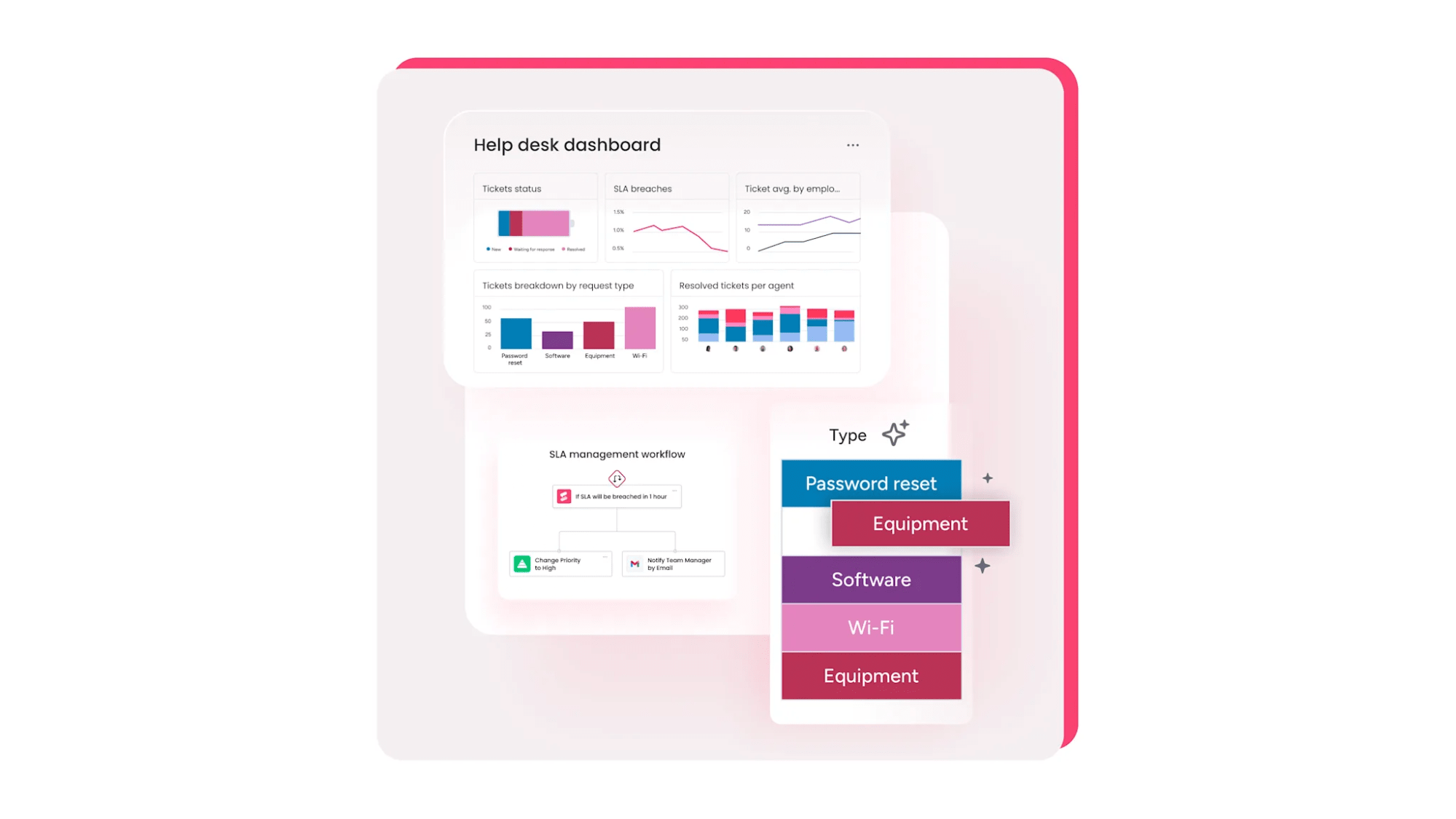
Transform your IT security management with monday service
Managing IT security requires more than just deploying the right tools — you need seamless coordination between security teams and the rest of your organization. With monday service, you bridge this gap with intelligent workflows that connect security operations to your broader business, while AI in customer service helps address customer concerns with increased efficiency.
AI that accelerates security incident resolution
The monday service platform uses AI to automatically categorize and route security incidents based on type, severity, and impact. This intelligent routing ensures critical threats get immediate attention while routine issues are handled efficiently.
The platform’s AI learns from your incident patterns, suggesting resolution steps and identifying recurring problems. This speeds up response times while helping you address root causes.
Seamless integration with your security stack
Your security tools generate valuable data, but it often stays trapped in silos. Connection capabilities in monday service allow you to connect with your existing security platforms through APIs and webhooks, creating a unified operational view.
This integration means security alerts automatically create tickets, updates sync across systems, and everyone stays informed without switching between multiple platforms.
Real-time security analytics and reporting
Clear visibility drives better security decisions. Dashboards in monday service are customizable, displaying security metrics, incident trends, and team performance in real-time.
Automated reporting ensures you’re always ready for compliance audits. Different stakeholders can access views tailored to their needs — executives see high-level trends while security teams dive into operational details.
With the right IT security solutions, and monday service powering your response, your organization can stay resilient, compliant, and confident.
Get started with monday service today.
Try monday service IT security refers to the specific technologies and tools that protect digital assets, while cybersecurity encompasses the broader strategy, policies, and practices for managing security risks. IT security is the "what" (tools), while cybersecurity is the "how" (strategy). Small businesses typically spend between $500-$2,000 per month on comprehensive IT security solutions, depending on company size and industry requirements. This investment covers essential protections like endpoint security, email filtering, and basic monitoring capabilities. AI-powered security solutions enhance human capabilities rather than replacing security teams entirely. While AI excels at pattern recognition and automated response, human expertise remains essential for strategic planning, complex incident investigation, and security policy development. The most common cyberattacks targeting businesses include phishing emails that trick employees into revealing credentials, ransomware that encrypts files for ransom payment, and business email compromise where attackers impersonate executives to authorize fraudulent transactions. Enterprise IT security solution implementation typically takes 3-6 months for full deployment, including planning, configuration, testing, and training phases. Cloud-based solutions can often be operational within weeks for basic functionality, with advanced features rolled out gradually. Businesses without IT security solutions face severe risks including data breaches that expose customer information, ransomware attacks that halt operations, regulatory fines for non-compliance, and lasting damage to reputation that drives away customers and partners.
FAQs
What is the difference between IT security and cybersecurity?
How much should a small business budget for IT security solutions?
Can AI-powered security solutions replace human security teams?
What are the most common types of cyberattacks businesses face?
How long does it take to implement enterprise IT security solutions?
What happens if my business doesn't invest in IT security solutions?
