Vendor partnerships can drive innovation and efficiency, but they also introduce risk. A single third-party failure, security breach, or compliance issue can disrupt operations, drain resources, and damage customer trust. Without a clear evaluation framework, these vulnerabilities remain hidden until it’s too late.
A vendor risk assessment template brings order to that complexity. It standardizes how you evaluate vendors across security, compliance, and operational criteria, transforming guesswork into measurable insights. The result is a transparent, repeatable process that strengthens accountability and builds resilience across your vendor network.
In this guide, you’ll learn how to structure effective assessments, choose the right template for your needs, and implement automation that keeps risk management consistent as your business scales.
Key takeaways
- Match assessment depth to vendor risk: use simplified templates for low-risk vendors and comprehensive evaluations for those handling sensitive data.
- Require evidence, not just answers: ask for certifications, audit reports, and process documentation instead of yes/no questions.
- Automate to scale effectively: use monday work management to centralize dashboards, distribute assessments, and monitor risks in real time.
- Score consistently: implement numerical scales that transform subjective reviews into comparable data points.
- Reassess regularly: schedule annual reviews for low-risk vendors and quarterly assessments for high-risk partners.
What is a vendor risk assessment template?
A vendor risk assessment template is a standardized questionnaire that evaluates the security, operational, and compliance risks of working with third-party vendors. With many organizations now working with over 1,000 third-party vendors, this process is crucial for managing a complex and growing attack surface.
It’s a structured approach to gathering key information about how vendors protect data, maintain operations, and meet regulatory standards. By asking targeted questions on areas like cybersecurity, compliance, and financial stability, you gain the insights needed to make confident, well-informed decisions about your business partnerships.
These templates typically include sections on:
- Data security.
- Business continuity.
- Regulatory compliance.
- Financial health.
Each section contains targeted questions that reveal potential risks before they impact your organization.
Types of vendor risk assessment templates
Different vendor relationships require different levels of scrutiny. Your approach depends on what data they’ll access, which systems they’ll touch, and how critical they are to your operations.
Basic vendor risk assessment template
Basic templates work for low-risk vendors who don’t handle sensitive data or critical operations. These streamlined assessments focus on fundamental security practices and general compliance requirements.
You’ll find 20–30 questions covering essential areas like password policies, data encryption, and incident response procedures: they’re perfect for office suppliers, basic software vendors, or consulting firms with limited system access.
Comprehensive security assessment template
High-risk vendors need deeper evaluation. Comprehensive templates dig into technical security controls, audit results, and detailed documentation requirements.
These assessments can include 100+ questions about penetration testing, security architecture, and compliance certifications. Financial services and healthcare organizations use these templates for vendors handling sensitive customer data or critical infrastructure.
Third-party risk assessment template
Third-party templates look beyond cybersecurity to evaluate total vendor risk. They assess financial stability, operational resilience, and strategic alignment with your business goals.
Key evaluation areas include:
- Financial health: credit ratings, insurance coverage, and business continuity funding.
- Operational capacity: service delivery capabilities and disaster recovery plans.
- Geographic risks: location-based vulnerabilities and regulatory considerations.
- Subcontractor management: how vendors oversee their own third parties.
Supplier risk assessment template
Supplier risk assessment templates focus on vendors critical to your production or service delivery. They emphasize operational reliability, quality control, and supply chain resilience.
For example, manufacturing companies evaluate production capacity, quality certifications, and raw material sourcing. On the other hand, service organizations may assess delivery performance, capacity management, and operational dependencies.
Try monday work managementHow to create your vendor risk assessment template
Building an effective template starts with understanding your specific risks and requirements, which is central to enterprise risk management. What works for a tech start-up won’t work for a healthcare provider or financial institution.
Follow these steps below to create a template that works for your organization:
Step 1: identify critical risk categories
Map the risks that matter most to your organization. Start with your industry’s regulatory requirements, then add risks specific to your operations and data sensitivity.
Common risk categories include information security, data privacy, operational continuity, and regulatory compliance. Healthcare organizations emphasize HIPAA requirements. Financial services focus on SOX compliance and data protection.
Modern platforms like monday work management helps teams collaborate on risk identification using customizable boards. You can assign risk categories to different stakeholders, track assessment progress, and maintain a central repository of vendor information.
Step 2: develop assessment questions
Create questions that require evidence, not just promises. Skip the yes/no format and ask for documentation, certifications, or detailed process descriptions.
Structure questions to gather both current state and future commitments. Ask about existing security certifications and planned improvements over the next 12 months.
It’s also important to focus on questions that differentiate vendors. Generic questions produce generic answers. Instead, probe specific areas where vendor capabilities vary significantly.
Step 3: establish scoring methodology
Consistent scoring turns subjective assessments into comparable data. Use numerical scales, risk levels, or weighted scoring based on question importance.
Create decision matrices linking scores to actions. High scores might trigger automatic approval. Low scores could require additional review or risk mitigation plans.
Document your scoring rationale. This consistency helps different evaluators reach similar conclusions and supports audit requirements.
Step 4: design review workflows
Define who does what in your assessment process, including designating a risk owner if necessary. Assign roles for distributing assessments, reviewing responses, and making final decisions.
Build review stages that include relevant experts. Security teams evaluate technical controls. Legal reviews compliance. Business stakeholders assess operational impact.
Finally, set realistic timelines with automated reminders: this keeps assessments moving without constant manual follow-up and supports consistent risk tracking across vendor relationships.
Essential questions for vendor risk assessments
The right questions uncover how vendors operate beneath the surface — exposing gaps that basic reviews might miss. An effective assessment mirrors the precision of risk analysis in project management, focusing on evidence-based evaluation rather than assumptions.
Each question category below targets a specific risk dimension, from data security and compliance to financial stability and business continuity, helping you build a complete view of every vendor’s reliability.
Information security questions
Security forms the foundation of vendor risk assessment, as these questions uncover how vendors protect your data and respond to threats. The financial stakes are high; insecure third-party connections accounted for 31% of all cyber insurance claims in 2024, highlighting the importance of thorough vetting.
- What encryption standards do you use for data at rest and in transit? This reveals technical security maturity.
- How do you manage user access and authentication? Strong access controls prevent unauthorized data exposure.
- Do you conduct regular vulnerability assessments and penetration testing? Proactive testing indicates serious security commitment.
- What is your incident response process? You need to know how quickly vendors detect and respond to breaches.
- How do you train employees on security? Human error causes many breaches, making training critical.
Business continuity questions
Can your vendor maintain services during disruptions? These questions assess operational resilience and recovery capabilities, which you can formalize with a business continuity plan template if needed.
- Do you maintain documented disaster recovery plans? Written plans show serious preparation.
- How often do you test business continuity procedures? Regular testing validates plan effectiveness.
- What are your recovery time objectives? Specific targets help you evaluate if vendor capabilities meet your needs.
- Do you maintain geographic redundancy? Multiple locations reduce single-point-of-failure risks.
Compliance and regulatory questions
Compliance questions verify vendors meet your regulatory requirements. They’re especially critical in regulated industries.
- Which regulatory frameworks do you comply with? Understanding scope helps identify potential gaps.
- Can you provide recent audit reports? Third-party validation confirms compliance claims.
- How do you handle data privacy requests? Privacy law compliance requires specific procedures.
- Are there any pending legal actions? Outstanding issues may indicate compliance problems.
Financial stability questions
Financial health impacts vendor longevity and service continuity. These questions assess business viability.
- Can you provide financial statements or credit ratings? Transparency indicates stability.
- What insurance coverage do you maintain? Adequate coverage protects both parties.
- How do you manage subcontractors? Supply chain management reveals indirect risks.
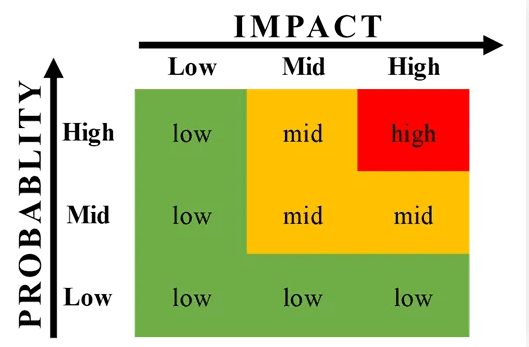
Vendor risk scoring with risk matrix templates
Risk matrix templates turn assessment results into clear, visual priorities. By mapping likelihood against impact, they help teams focus on the risks that matter most.
Below, you’ll learn how to build your own matrix and assign consistent risk levels that guide response actions and strengthen vendor oversight.
Creating your risk matrix
Start by mapping likelihood (from rare to almost certain) against impact (from insignificant to catastrophic). The intersections create clear action zones that guide how your team responds:
- Low risk: accept and monitor periodically.
- Medium risk: apply targeted controls and review regularly.
- High risk: act immediately or consider alternate vendors.
Work management solutions such as monday work management make this process dynamic. Dashboards visualize vendor risks across your portfolio, track score changes automatically, and send alerts to keep leadership informed in real time.
Assigning risk levels
Map assessment scores to matrix positions using consistent criteria. Weight different risk categories based on business priorities.
Develop response strategies for each risk level. Low risks might need quarterly reviews. High risks could trigger enhanced monitoring or contract renegotiation.
Create escalation triggers. When vendors move to higher risk categories, automated notifications ensure quick response.
7 best practices for vendor risk assessment
Smart vendor risk management balances thoroughness with efficiency. The practices outlined beneath help you build a sustainable assessment program:
1. Standardize your assessment process
Consistency enables fair comparisons and reduces assessment time. Use the same templates and scoring for similar vendor types.
Create vendor tiers based on risk levels. High-risk vendors get comprehensive assessments. Low-risk vendors receive streamlined evaluations.
2. Automate vendor communications
Manual follow-up wastes time. Automated workflows handle assessment distribution, reminders, and escalations.
Set up triggered communications based on vendor actions. Incomplete assessments generate reminders. High-risk responses trigger immediate reviews.
3. Schedule regular reviews
Vendor risks change over time. Annual assessments work for most vendors. Critical vendors need quarterly or semi-annual reviews.
Monitor external triggers for unscheduled assessments. Security breaches, financial troubles, or regulatory changes should prompt immediate re-evaluation.
4. Involve key stakeholders
Effective assessment requires multiple perspectives. Security evaluates technical controls. Legal reviews compliance. Business assesses operational impact.
Define clear roles and decision authority to prevent delays, which is critical when research shows a major perception gap exists between senior leaders (45%) and individual contributors (23%) on how well change is managed.
5. Document all findings
Comprehensive documentation supports audits and future assessments. Record responses, decisions, and mitigation actions in a risk register to ensure a complete and auditable trail.
Create standardized templates capturing key information consistently. This simplifies vendor comparisons and trend analysis.
6. Create action plans
Generic recommendations don’t drive improvement. Develop specific remediation plans with timelines and success metrics.
Work with vendors on realistic improvement timelines. Monitor progress and adjust plans based on results.
7. Monitor continuously
Risk assessment isn’t a one-time event. Ongoing monitoring catches emerging risks between formal reviews.
Track performance indicators reflecting vendor health. Set thresholds triggering additional investigation when metrics decline.
Building automated vendor risk workflows
As vendor networks expand, managing assessments manually becomes unsustainable. Automation brings structure and consistency, ensuring every vendor follows the same evaluation and review process without adding administrative burden.
Below, you’ll see how workflow automation improves efficiency, strengthens accountability, and connects seamlessly with your broader procurement and compliance systems.
Workflow automation benefits
Automation transforms vendor risk management in several ways. It reduces processing time, ensures consistent follow-up, and improves vendor experience through predictable interactions.
Key automation capabilities include:
- Automated distribution: send assessments based on onboarding or review schedules.
- Response tracking: monitor completion and send escalating reminders automatically.
- Intelligent routing: direct assessments to appropriate reviewers based on responses.
- Automated scoring: calculate risk scores and generate reports without manual work.
Integration strategies
Connecting your assessment workflows with procurement, security, and compliance systems ensures complete visibility across the vendor lifecycle. Real-time integrations eliminate data silos, allowing risk scores and assessment results to update automatically across platforms.
With platforms like monday work management, these integrations become part of a unified process. Vendor onboarding, ongoing monitoring, and mitigation activities all connect within one scalable system — keeping every stakeholder aligned and every assessment up to date.
Transform vendor risk management with monday work management
Growing organizations need more than spreadsheets to manage vendor risk effectively —especially when only 71% of employees in the largest enterprises report using their company’s work management software.
It’s also really important to transition to a modern and dynamic platform like monday work management that offers several helpful features:
Centralized vendor dashboards
Real-time dashboards show vendor assessment status, risk scores, and remediation progress across your entire portfolio. Different stakeholders see relevant information without manual reporting.
Executive views highlight portfolio risk trends. Security teams track technical assessments. Procurement monitors completion rates.
Automated assessment workflows
Intelligent automation manages the complete assessment lifecycle. Conditional logic routes assessments based on vendor type and risk level.
Vendors receive clear instructions and deadlines. Internal teams get notifications about pending reviews. Everything flows smoothly without manual intervention.
Real-time risk monitoring
Continuous monitoring tracks vendor performance between formal assessments. AI-powered insights identify emerging risks before they impact operations.
Risk scores update dynamically as new information arrives. Stakeholders receive immediate alerts when vendor profiles change significantly.
Collaborative risk reviews
Cross-functional teams review assessments efficiently using shared workspaces. Comment threads, file sharing, and approval workflows keep everyone aligned: helping to integrate project risk management with vendor oversight.
Audit trails also document all activities automatically. This comprehensive record supports compliance requirements without manual documentation.
Try monday work managementFrequently asked questions
How often should vendor risk assessments be conducted?
The frequency of vendor risk assessments depends on risk level. They should typically be conducted annually for low-risk vendors and quarterly for high-risk vendors handling sensitive data. The frequency could also increase based on regulatory requirements, vendor operational changes, or emerging security threats specific to your industry.
What is the difference between a vendor risk assessment and vendor due diligence?
A vendor risk assessment is an ongoing evaluation of specific security, operational, and compliance risks throughout the vendor relationship. Vendor due diligence is a one-time, comprehensive evaluation before contract signing that includes financial viability, legal standing, and overall business capabilities.
Can small businesses use the same vendor risk assessment templates as large enterprises?
Small businesses can adapt enterprise templates by focusing on critical risk categories relevant to their operations. They should prioritize essential security and compliance questions while removing complex technical assessments that don't apply to their vendor relationships or available resources.
How do you ensure vendor compliance with risk assessment requirements?
Vendor compliance requires contractual obligations for assessment participation, regular monitoring of response completeness, and clear escalation procedures. Organizations should establish consequences for non-compliance, including contract review or termination clauses for persistent non-participation.
Which industries have specific vendor risk assessment requirements?
The healthcare, financial services, and government sectors have the most stringent requirements due to HIPAA, SOX, PCI DSS, and FedRAMP regulations. These industries must ensure vendors meet specific security standards, undergo regular audits, and maintain detailed risk management documentation.
What should be included in a vendor risk assessment questionnaire?
A vendor risk assessment questionnaire should include questions about information security controls, data handling practices, compliance certifications, business continuity plans, and incident response procedures. Questions should align with your industry requirements, regulatory obligations, and the sensitivity of data the vendor will access.
